Configuring Dynamic Link Scanning (Link Lock)
What is Dynamic Link Scanning (Link Lock) and How Does It Work?
Dynamic Link Scanning (known as Link Lock within UpStream, as well as Click-Time Verification, Link Rewriting or SafeLinks in other environments) is a post-filter email security service that protects against time-of-click and dynamic email attacks. Traditionally, anti-phishing and anti-virus security engines audit each incoming email for known threats, followed by advanced analyses within a sandbox environment. If the email is deemed safe, it’s delivered to the recipient’s inbox.
But what if an attacker changes the email content after sandbox approval?
These sophisticated cyberattacks insert malicious content into an email’s payload after delivery. Completely innocuous links can be swapped with malware, drive-by downloads, and credential-harvesting links post-delivery. These attacks can occur through endpoint compromise, MITM (Man-in-the-Middle) attacks, ROPEMAKER exploits, and other more sophisticated tactics. No matter the maneuver, the end result is the same: “safe” links can be transformed into malicious content.
For example:
An employee receives a spoofed email from a trusted vendor with a link to an invoice. The link passed initial virus scans but is swapped with a malicious link upon delivery. When clicked, the link installs ransomware on the employee’s computer.
Human Resources sends an email including a link to a new company policy document. An attacker intercepts this email in transit and alters the link to redirect to a false login page. After recipients click the link, the attacker is able to harvest sensitive login credentials.
Dynamic Link Scanning offer continuous, real-time protection as soon as an email is delivered to a recipient’s inbox. All inbound links are automatically rewritten (encoded in our verification service URL) prior to delivery and scanned for security at the time of click. As soon as a link is clicked, the service checks for safety in real time. If a link is deemed malicious, the recipient will be redirected to a warning page specifying the danger and options for proceeding. It doesn’t matter when the email was received or the link clicked– these protections remain continuously active.
Optionally, organizations can set an “allowed URLs” list at the domain or individual user levels to prevent rewriting of the URLs and the pre-scanning that can “trigger” access-specific actions to an email, such as an emailed MFA token or password reset email that only allows a single viewing.
Understanding the Hierarchy of Link Lock
Dynamic Link Scanning (Link Lock) can be enabled and configured on the Domain and User levels independently.
These levels are hierarchical:
If a rule is set at the Domain level, all users within the domain are affected.
This begins engaging Dynamic Link Scanning for all users within the domain selected and is the recommended approach.
If there are multiple domains under a given organization’s administration, each domain must be configured individually and can have its own independent Link Lock policies.
If a rule is set at the User level, only the specified user is affected.
This is great for high-risk users when the Domain-wide option cannot be used for internal reasons.
Enabling Link Lock for the Entire Domain
The most common use case of deploying Link Lock is for the entire domain, meaning that all users within the specified domain will be protected by Link Lock’s post-delivery scanning and protection. The procedure below will walk through this process.
Note: If there are multiple domains belonging to the organization being filtered by UpStream, this same procedure should be repeated for all of the domains to ensure complete protection.
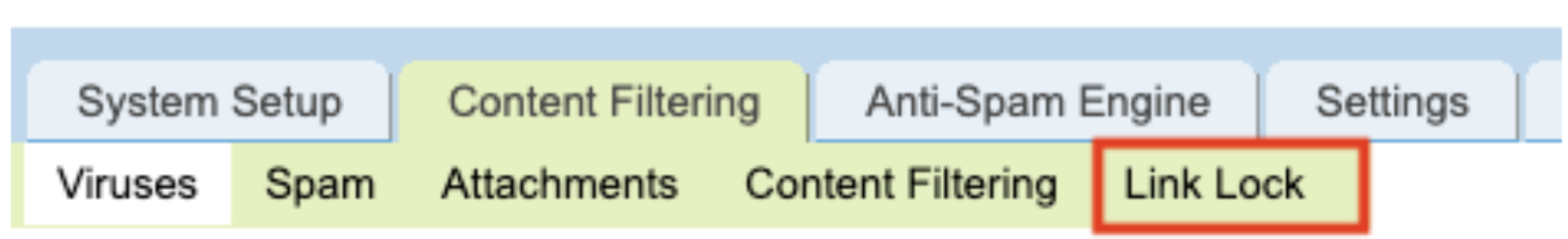
To begin, log into the UpStream system that hosts your domain. From the UpStream homepage, click Content Filtering from the top navigation bar.
Next, select Link Lock from the green menu that appears.
Scroll down to the section titled Configuration.
In the Domains panel, enter in the domain(s) that Link Lock should be enabled for. Under the Options column, click the pencil icon of the selected domain.
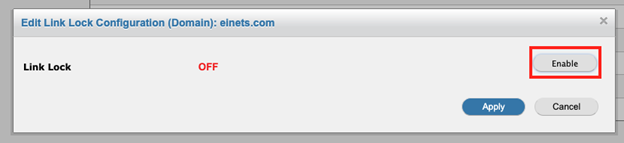
A pop-up will appear. To enable Link Lock, click the gray Enable button.
This will enable Link Lock for the selected domain.
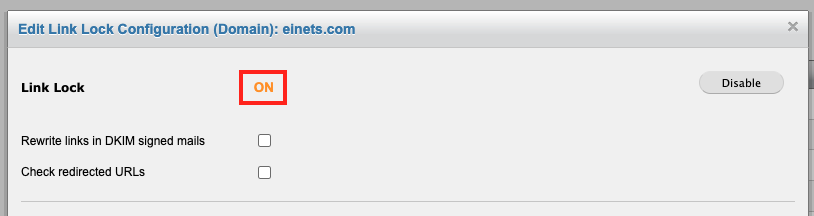
The Link Lock configuration page will appear. To confirm that Link Lock has been enabled successfully, confirm that a yellow ON appears to the right of the Link Lock section.
With Domain-wide Link Lock now enabled, please skip ahead to the Configuration Link Lock Options and Block Page section. This will discuss advanced options like the rewriting of DKIM signed emails and much more.
Enabling Link Lock for an Individual User
In some cases, often when there may be political pushback or confusion from end users, it may be preferable to enable Link Lock for a single user (rather than at the Domain level). This is especially useful for high-risk users like management, ownership, financial staff (particularly Accounts Payable) and any users who have experienced cybersecurity troubles in the past or are highly likely to in the future.
To begin, log into the UpStream system that hosts your domain. From the UpStream homepage, click Content Filtering from the top navigation bar.
Next, select Link Lock from the green menu that appears.
Scroll down to the section titled Configuration.
Then, find the Users section. Here, there is a list of all users eligible for Link Lock enablement.
Find the user that Link Lock will be enabled for.
Note: If many users are listed, use the Filter User search bar to easily find the selected user.
Under the Options column, click the pencil icon next to the selected user.
A pop-up will appear. To enable Link Lock, click the gray Enable button.
This will enable Link Lock for the selected user.
A yellow ON will appear showing that Link Link is now active.
Additional options, like DKIM signed email link rewriting, will be discussed directly below.
To apply these changes, click the blue Apply button.
Configuring Link Lock Options and Block Page
Additional optional link rewriting options become available after enablement of Link Lock:
Rewrite Links in DKIM Signed Emails allows UpStream to rewrite links in DKIM signed emails, which will break the chain of trust that comes from this. It is recommended to not enable this feature, as doing so will invalidate DKIM signatures and creates a higher risk of the message being marked as spam by other filtering rules on the system (if configured). As DKIM becomes a widely accepted security standard, it is recommended to keep these signatures intact.
Note: DKIM stands for DomainKeys Identified Mail. It’s an email authentication method that allows the receiver to check that an email coming from a specific domain is authorized by the domain’s owner. DKIM was designed to help prevent email spoofing.
Check Redirected URLs allows Link Lock to follow redirected URLs (a link that lands on another page which then relinks to another page) to ensure that the redirected landing page is also safe. Checking redirected URLs will check relinks up to five hops down from the original link. Activating Check Redirected URLs can slow mail delivery as the multiple checks do take a little more time to execute.
Check Redirected URLs is recommended as a prudent feature to activate, although mail speed delivery should be analyzed afterwards to ensure it is workable for the organization’s end users.
Next, customize the settings for Link Lock’s presentation to the end users. This includes editing the Block Page’s logo and messaging (the page that appears when a malicious link is detected), as well as selecting the allowed actions for the User after a threat is detected.
A breakdown of the various options and what they mean are below.
Use custom logo:
Select this box if a custom organization-specific logo is preferred. The default SpamTitan logo will be used otherwise.
It is highly recommended to use the local organization’s logo to help users identify that the Block Page is being sent to them by their local IT staff, rather than a service they may be unfamiliar with.
Logo:
This field displays the image currently being used on the Block Page.
Upload new logo:
Select Choose File to upload a custom Block Page image. The recommended size for the logo is 500 pixels wide by 125 pixels high.
Use custom message:
Select this box to enable customization of the Block Page’s header and message to the end user.
Message header:
Enter a custom header for the block page. This can be customized according to your organization’s internal policies, wording preferences and user behavior.
The default header is “Access Blocked.”
Examples of what this could be could be changed to that offer more context, depending on how users respond to block pages, is below:
“Warning: Malicious Content Detected on this Website.”
“This URL may not be safe. Please review the below guidance for how to proceed.”
Message body
Enter a custom message for the Block Page. This can be customized according to your organization’s internal policies, wording preferences, and user behavior.
The default message is “This website has been blocked as it is classified as malicious.”
Examples of what this could be could be changed to that offer more context, depending on how users respond to block pages, is below:
“Malicious content has been detected in this URL. This could lead to malware installation, phishing attacks, credential/identity theft and more. Access to this link has been blocked: please contact our IT team for more information.”
“Our security software has determined that this URL contains malicious content. Please proceed with extreme caution or return to the previous page.”
“Access to this URL has been Blocked. As a reminder, do not click on suspicious links from unusual sender addresses, requests for personal information, strange file downloads, or anything out of the ordinary. If you are unsure of whether or not an email is safe, please contact the IT Team.”
Display blocked URL
This checkbox allows for the original URL to be displayed on the Block Page.
It is not recommended to allow this, since the user can then copy and paste the original malicious URL into a web browser, reach the website (assuming no web filter is present to block it) and still trigger the payload just as if Link Lock had not been enabled in the first place.
Show “Continue to Site” button
This checkbox adds a button to the Block Page that allows the user to click past the warning notification if they wish to do so or if they think the Block Page may be triggering in error.
It is not recommended to allow this, as if UpStream has determined the URL to be risky or malicious from the numerous data sources the service draws from, it is extremely undesirable to let an end user override that decision.
A couple of Block Page examples that are used regularly with UpStream are below, showing variants of the options that can be configured.
The first example is the recommended configuration:
An easy to identify logo for the user, strong command in the Header line telling them not to proceed (similar to any roadway sign or workplace safety signage), as well as additional context in the Message itself telling them why and whom to contact if they need assistance.
This second (not recommended) variant of the Block Page provides all of the previous steps, but also displays the exact URL that was blocked and has a classification showing why it wound up there, along with the bypass functionality that allows the user to continue on to the website if they choose to do so.
Once the Block Page configuration options are configured to preference, click on the Apply button at the bottom of the page to save the configuration.
In the event of a future need to disable Link Lock, clicking on the Reset to Default Settings section’s Reset button will immediately reset all Link Lock settings back to their defaults, along with disabling Link Lock itself.
Adding URL Exemptions
Specified URLs can be exempted from Link Lock scanning through the URL exemption list. This may be useful in select cases, such as:
The URL originates from a trusted internal source and has time sensitivity involved with using it, particularly common for email account-bound MultiFactor Authentication (MFA) prompts.
In the case of false positives, where a specific URL is frequently flagged as malicious (but is approved by the organization).
Sensitive emails that only allow for a single click to complete an action. These may include information/identifications verifications and password resets.
URLs that are already subject to another vendor’s URL Rewriting, such as Microsoft’s Safe Links or Barracuda’s Link Protection, which having duplicative layers of Dynamic Link Scanning upon is redundant and slows down the link launching process without significant increase in security.
URL exemptions can be specified at the Domain and User levels.
To set a URL exemption, click Content Filtering from the top navigation bar.
Next, select Link Lock from the green menu that appears.
Scroll down to the section titled Allowed URLs.
In this section there are two components:
Domain Allowed URLs: URLs exempted for all users within a particular domain.
User Allowed URLs: URLs exempted at the individual user level only.
Choose to set the URL exemption at the Domain or User level. Then, scroll down to that section.
To add a URL exemption, click the gray Add button at the bottom right of the section.
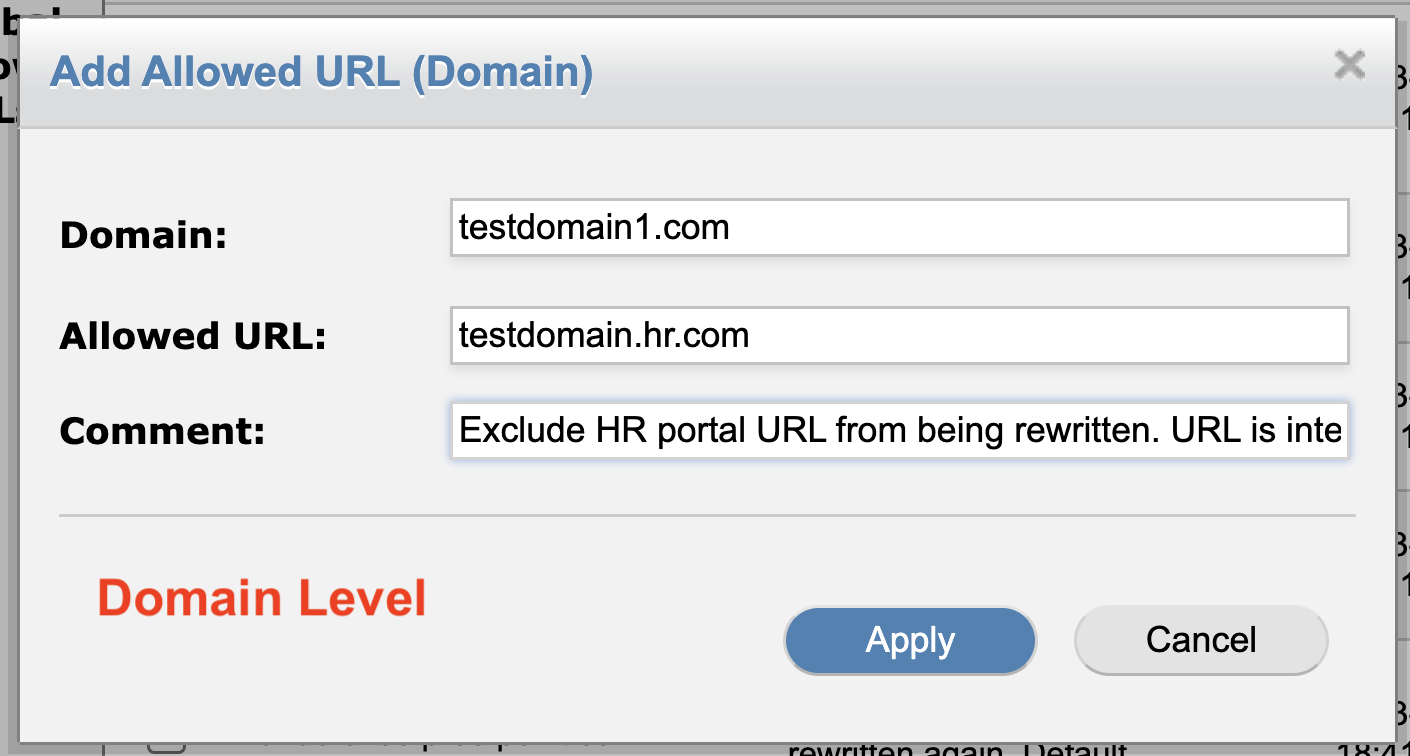
A pop-up will appear with multiple data fields. Be sure to populate all listed fields as appropriate for the exemption being granted.
Domain: “DomainNameToExemptHere.com”
User: “EndUser@domainname.com”
Allowed URL: The URL to be added to the exempt list.
Comment: Add an internal comment to remark why the URL was added to the exempt list.
Comment examples:
“Exclude Human Resources portal URL from being rewritten. URL is internal and deemed safe.”
“Exclude password reset emails from URL rewrites, as the links are limited to one click only.”
After filling out all fields, click the blue Apply button.
The exempt URL will now appear listed under the Allowed URL column.
To remove a URL from the exempt list, click the X icon on the far right of the URL’s row.
A green banner will appear, confirming the URL was successfully removed.